TryHackMe Anthem’s Walkthrough
Description
Anthem is beginner level windows room by Chevalier.This room offers lot of osint challenges and basic enumeration once we get on the box.As mentioned that this room is easy and very begineer friendly but some questions take lot of time to complete because hints are very confusing and directs you to totally different direction.Before doing this room, you have to know how to use nmap, what is robots.txt file, and how to connect to rdp service using rdp client.
Task 1
Nmap Scan
nmap -sC -sV -Av -oN nmap/anthem 10.10.139.243
-sC - run all the default scripts
-sV - find the version of all the service running on the target
-A - run the scan in aggressive mode
-v - show output in verbose mode
-oN - output to a file in nmap format
Output
# Nmap 7.80 scan initiated Sun May 17 19:47:35 2020 as: nmap -sC -sV -Av -oA nmap/anthem 10.10.139.243
Nmap scan report for 10.10.139.243
Host is up (0.50s latency).
Not shown: 994 closed ports
PORT STATE SERVICE VERSION
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
| http-robots.txt: 4 disallowed entries
|_/bin/ /config/ /umbraco/ /umbraco_client/
|_http-title: Anthem.com - Welcome to our blog
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
3389/tcp open ms-wbt-server Microsoft Terminal Services
| rdp-ntlm-info:
| Target_Name: WIN-LU09299160F
| NetBIOS_Domain_Name: WIN-LU09299160F
| NetBIOS_Computer_Name: WIN-LU09299160F
| DNS_Domain_Name: WIN-LU09299160F
| DNS_Computer_Name: WIN-LU09299160F
| Product_Version: 10.0.17763
|_ System_Time: 2020-05-17T14:19:26+00:00
| ssl-cert: Subject: commonName=WIN-LU09299160F
| Issuer: commonName=WIN-LU09299160F
| Public Key type: rsa
| Public Key bits: 2048
| Signature Algorithm: sha256WithRSAEncryption
| Not valid before: 2020-04-04T22:56:38
| Not valid after: 2020-10-04T22:56:38
| MD5: 2814 61de 95b7 e9b5 4789 3027 7f1f 60d2
|_SHA-1: d47d 2a8f 6143 b820 936e 4120 cdd1 9ddc 5385 d285
|_ssl-date: 2020-05-17T14:19:36+00:00; 0s from scanner time.
8701/tcp filtered unknown
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-05-17T14:19:26
|_ start_date: N/A
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun May 17 19:49:38 2020 -- 1 IP address (1 host up) scanned in 123.08 seconds
We get lot of information about the target from the above scan.Such as which service is running on which port.It also tells us about the domain name of the target. And it also finds that there is robots.txt file on the website.
Web Analysis
The website is blogging website which has 2 blog posts.
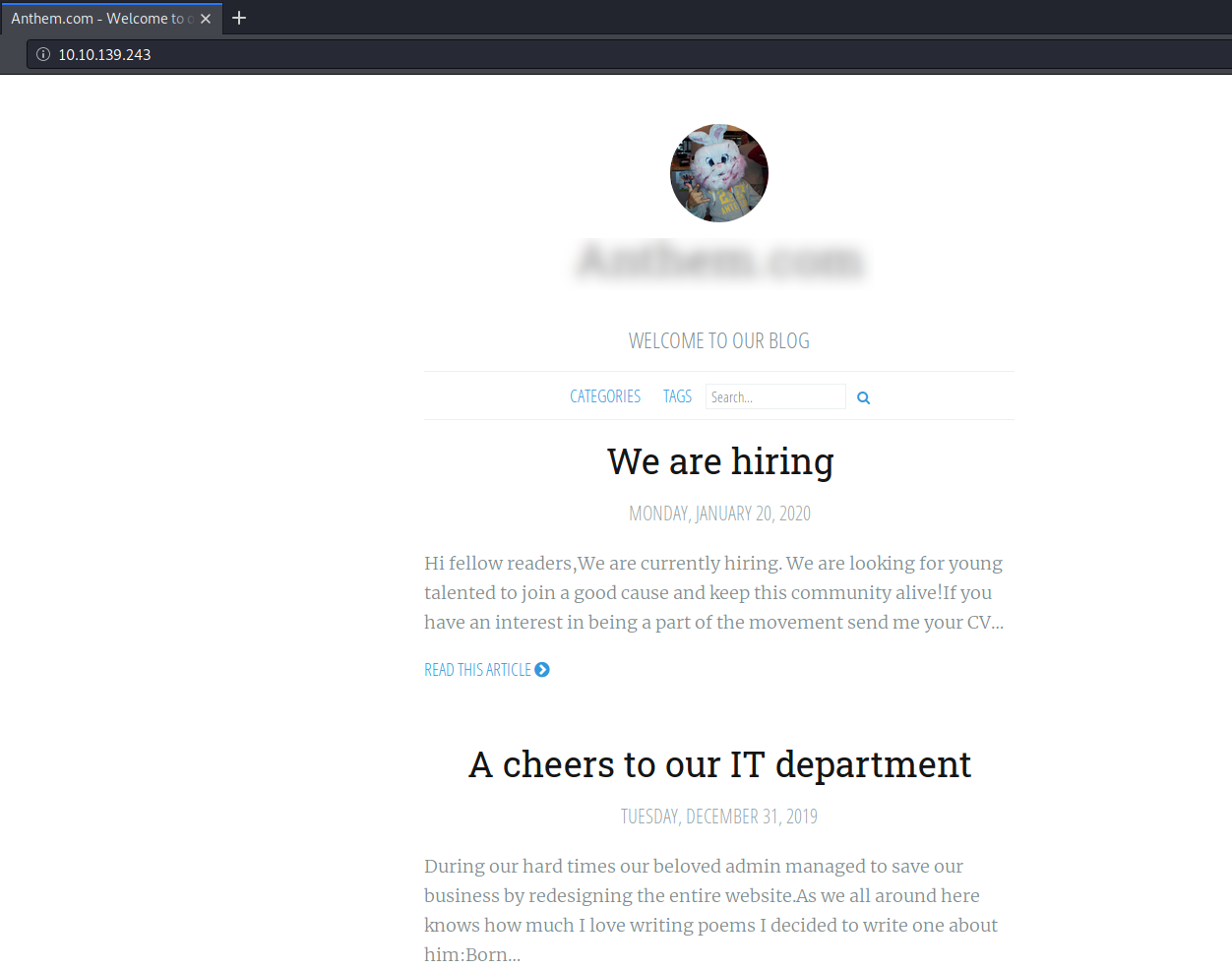
first lets visit the /robots.txt file that we found on the nmap scan.
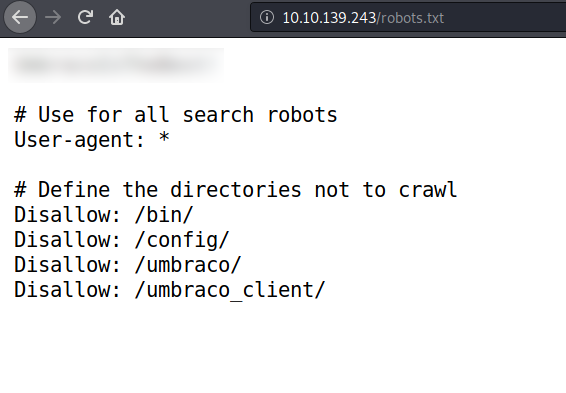
looks like we found a text which looks like a possible password for something, that is not found by the nmap scan.Nmap scan show us the four directories, lets try to go to the /umbraco one.
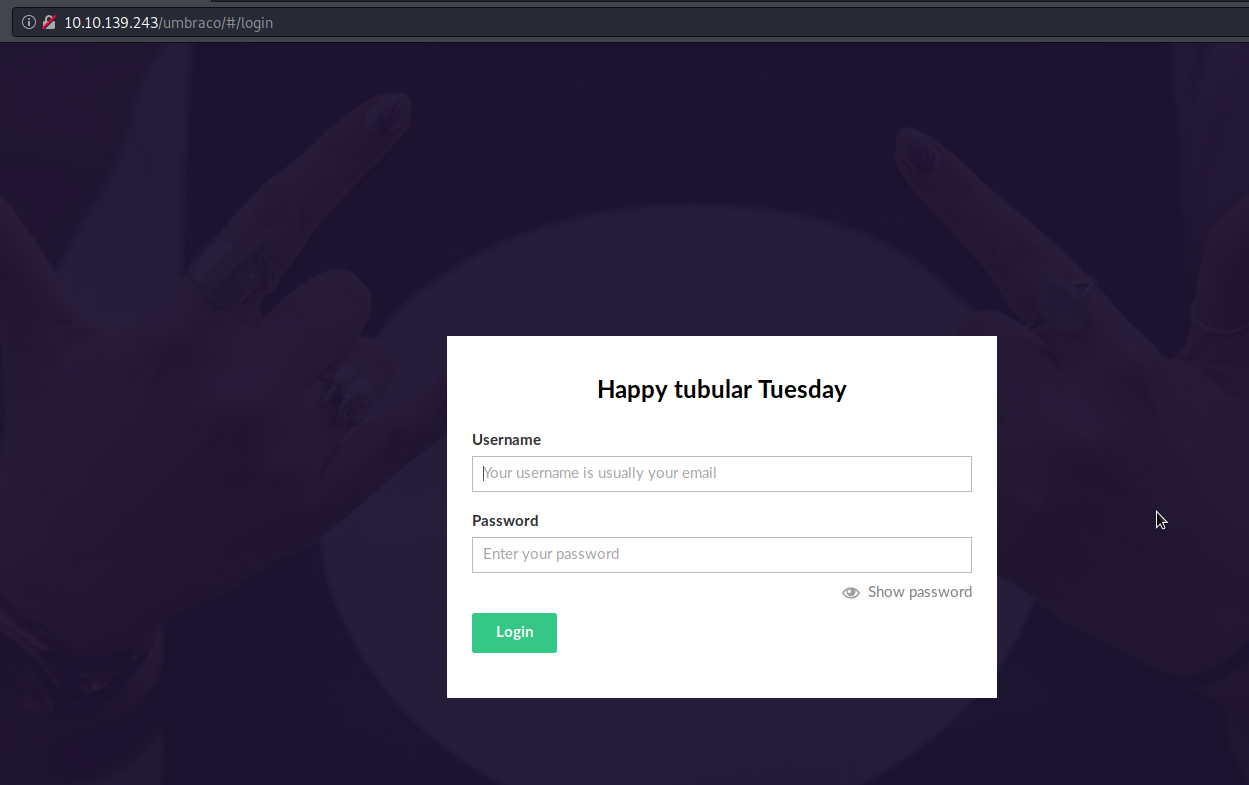
It looks like the login page for some kind a CMS for posting content to the webpage we found in homepage.But we don’t have the credential to log in.So we must look it after we find the credentials.
Lets try to find Potential user for this CMS login. If you look at the second blog post on the website, Its a poem about admin of the site.
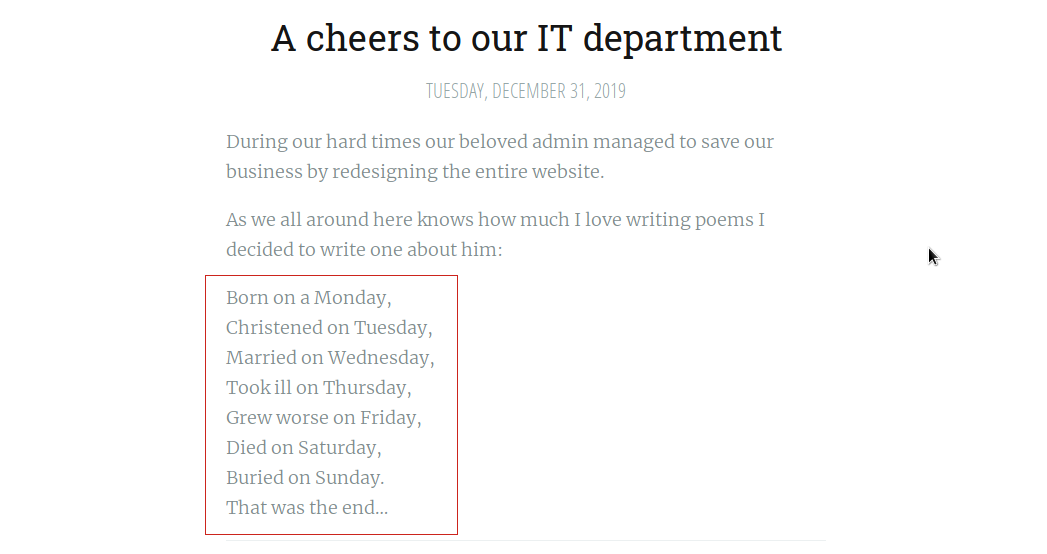
If you check the hints it says search on your favourite search engine, So lets just copy the whole poem and search it on the google (my favourite search engine) and we get the name of admin.
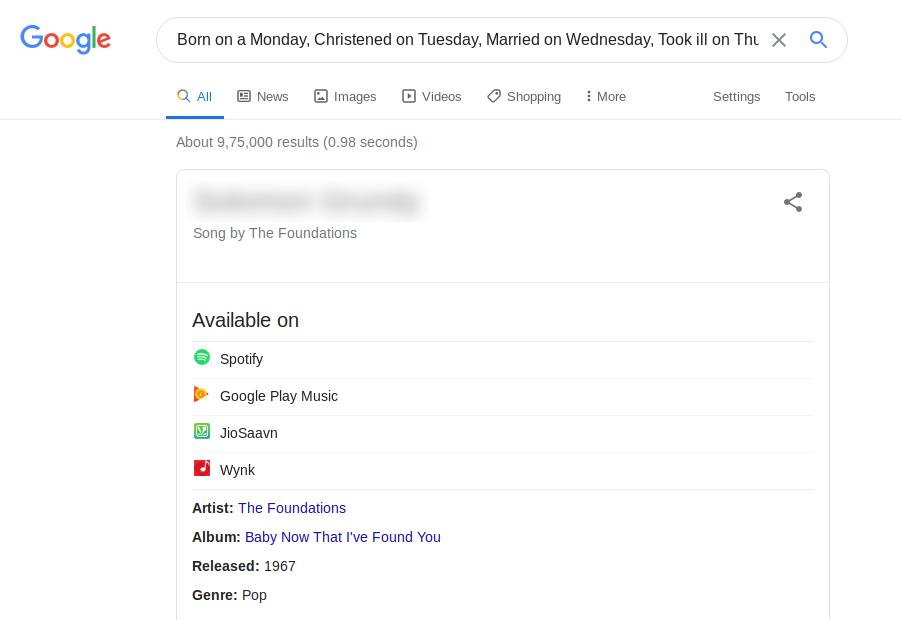
But the login page demands for email of the user.So lets find the email addres of the admin.If you check on the hints then it says there is an another email on the website which follows the pattern of admin’s email.And if you look at the first blog post on the website, it has email address of the author of the post which has the pattern of intials of user’s name @ domain name of the site.
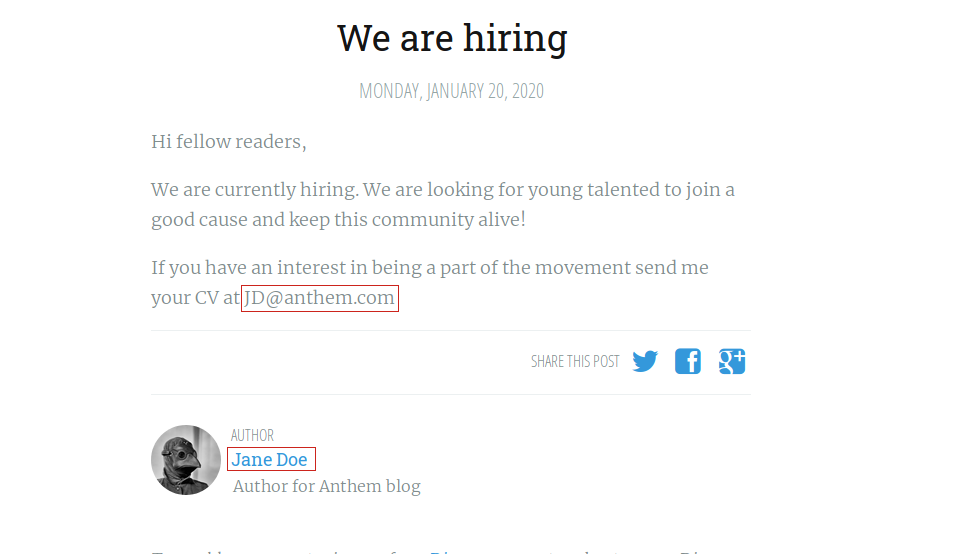
By following the above pattern we should get the email address of the admin.To check that you can try to log in on the CMS with that email address and password we found on the /robots.txt file.
Task 2
In task 2 we have to find all the flags that are hidden on the website.Actually if you look on the page source of each link that has reference on the website, you will find all the flags.The question and flag doesn’t have a connection to each other so you have to try to submit flags for all question and which one accepts it thats the correct question for that flag.
Flag 1
Flag 2
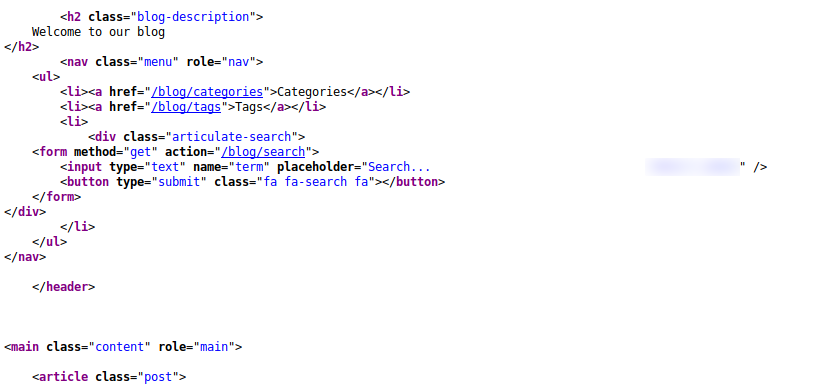
Flag 3
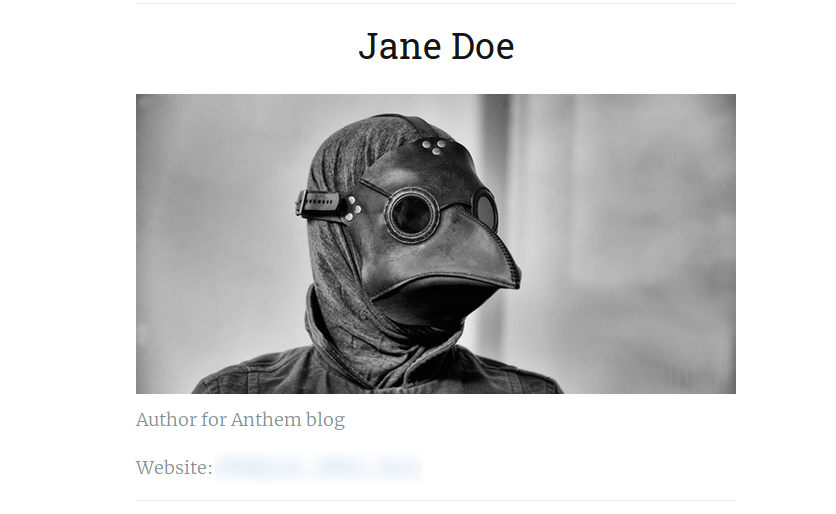
Flag 4
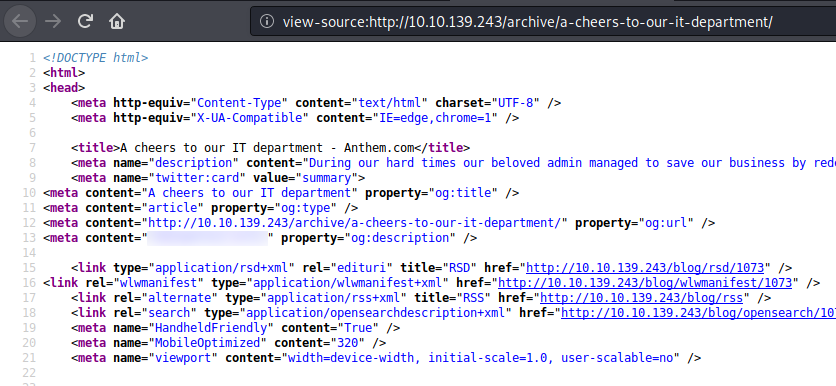
Task 3
On the task 3, we have to connect to the rdp service (Microsoft Terminal Service) that is running on the target machine by the credential we already found on the task 1. But the question says that the box is not on the domain so exclude the domain name from the username.
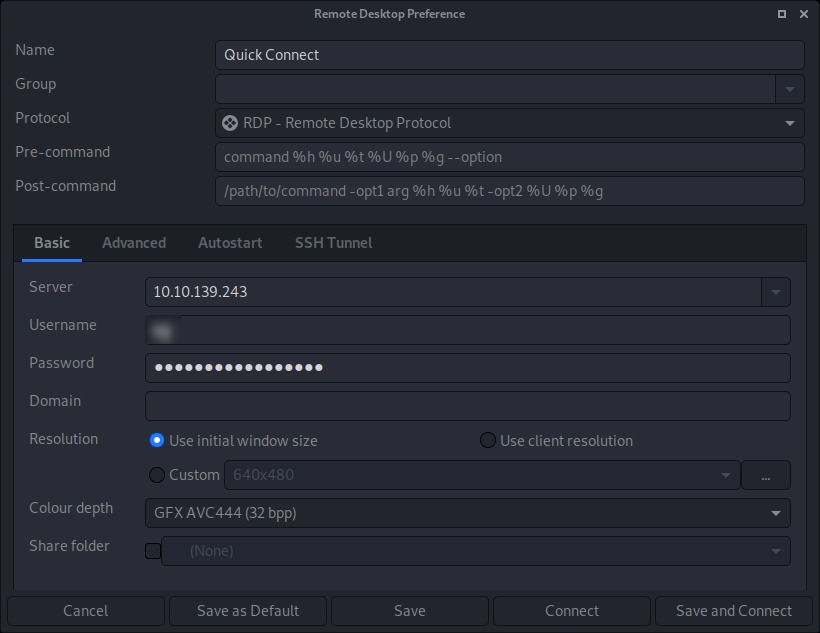
User Flag
Once we get on the box, we got the user.txt on the desktop of the user.
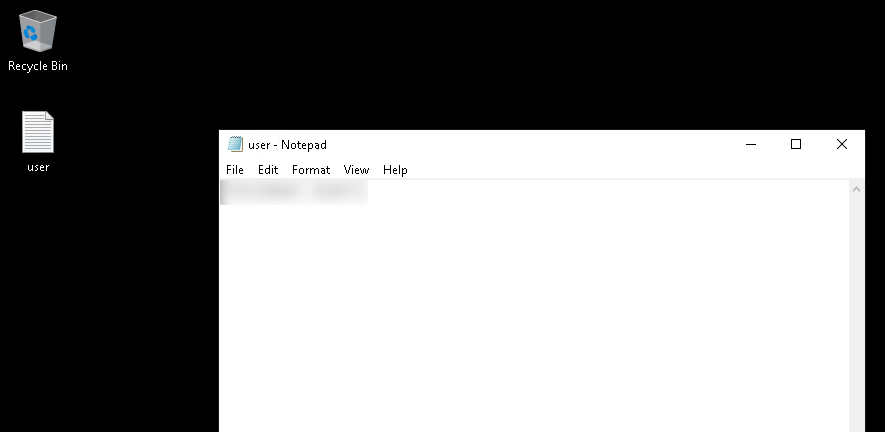
Administrator’s Password
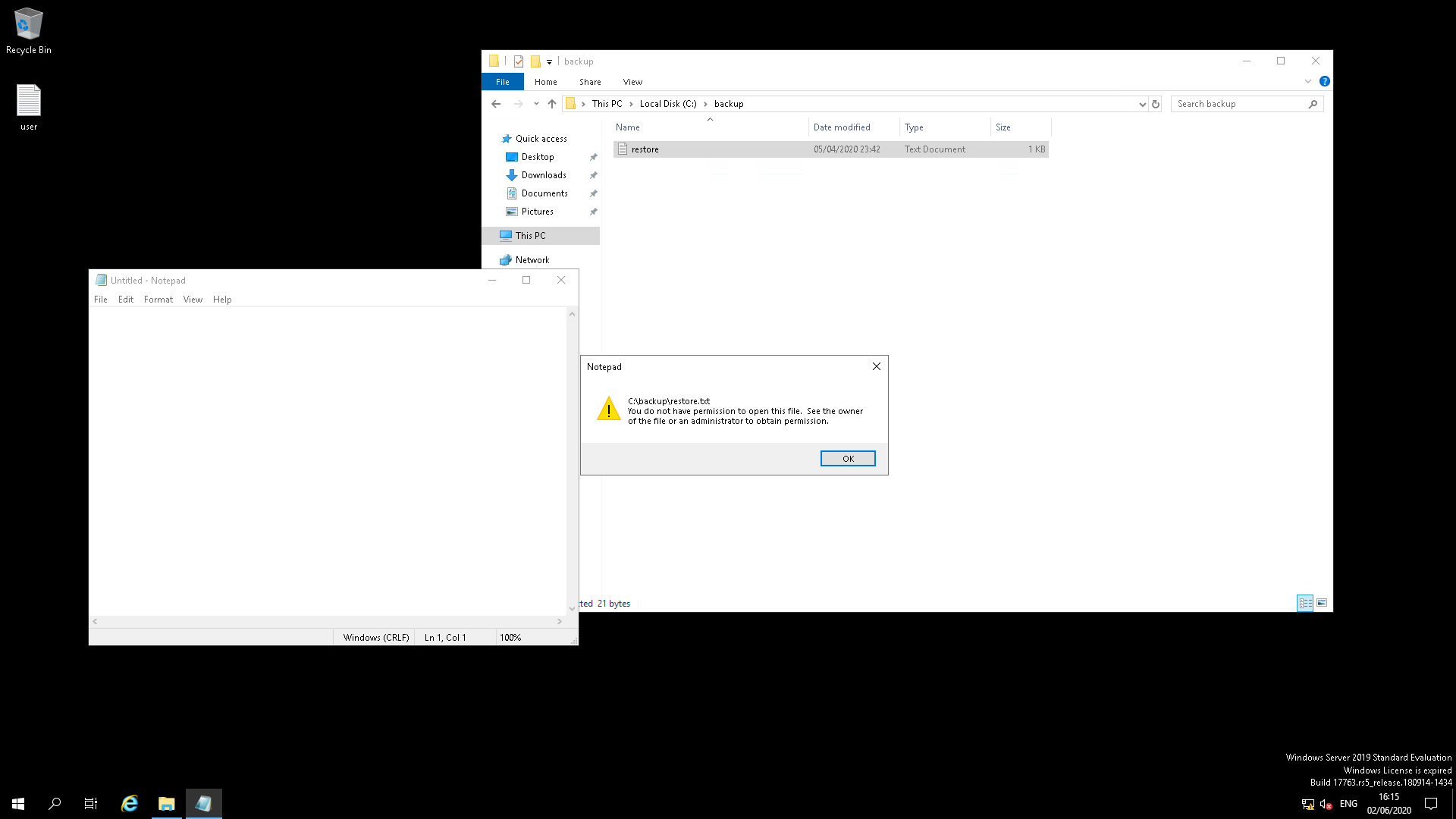
For getting the administrator privledge we have to find the administrator’s password.If check on hints it says it is hidden.So we have to enable the hidden option on the file explorer to find it.After doing that we found a backup folder on the C: drive which contains a restore file, if we try to open, we get permission denied.
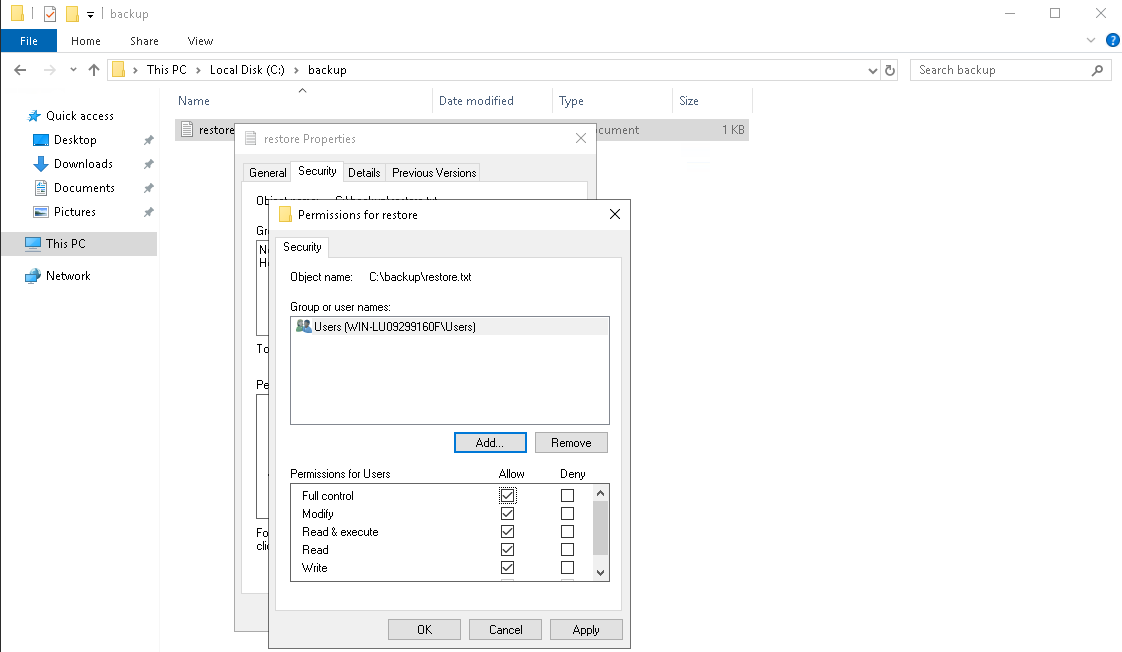
So we have to add our user group to the file’s property and grant all the permission over the file.
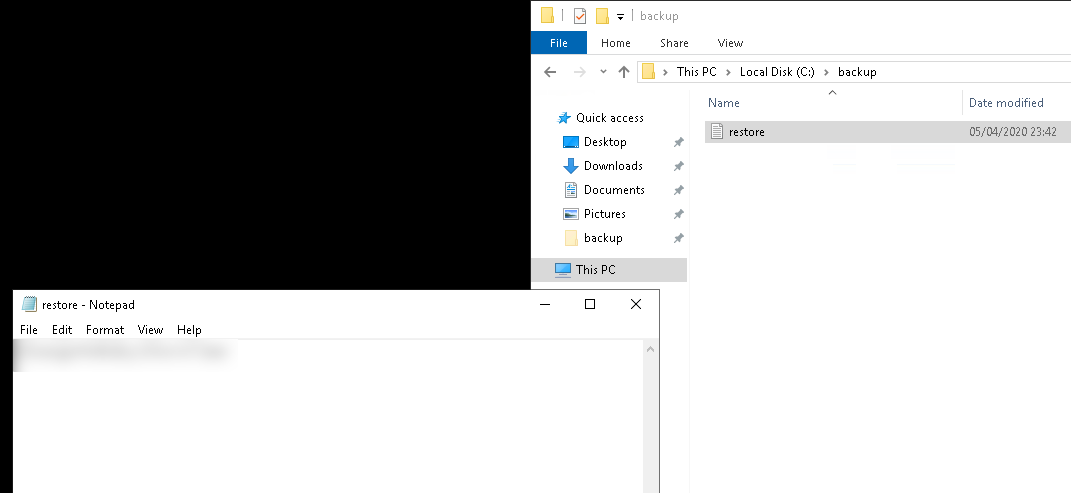
Now, we get to open the file to read it.And we got the administrator’s password.
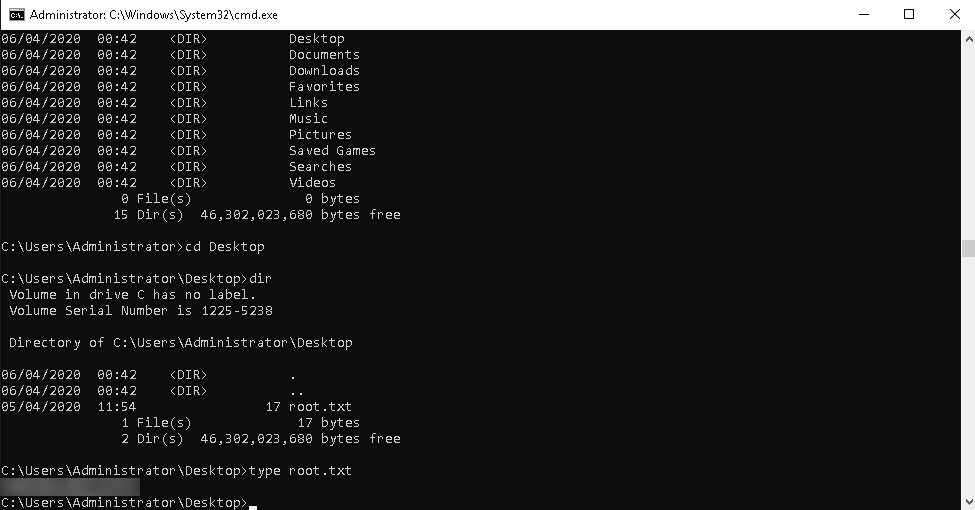
Root Flag
Open the CMD with administrator’s privledge get the root.txt on the desktop of the administrator.
Thanks for reading this walkthrough, If you like it please share it on twitter, reddit or in linkedin.